Blogs
It usage of has somewhat extended the fresh arrive at out of online casinos, attracting a wide listeners and causing the development of the gambling on line globe. Cryptologic slot online game are notable for their an excellent visuals in the on-line casino globe, to play a life threatening character inside their popularity. They feature epic animated graphics, high-quality sound files, and soundtracks made to improve the complete player sense, from the program on the added bonus features of for every video game. Cryptologic stands out from other on-line casino software company by offering nice earnings, a wide range of online game, and you will consistent game play.
- Including message franking, send tracing spends cryptographic codes to allow platforms observe where an email came from.
- Inside contour 1.step one they made the text safe because of the building they to the cipher text using a keen security algorithm and extra decoding for action.
- It’s a warranty your unique creator of your own research never refute the newest design otherwise sign of your said investigation to a person otherwise 3rd party.
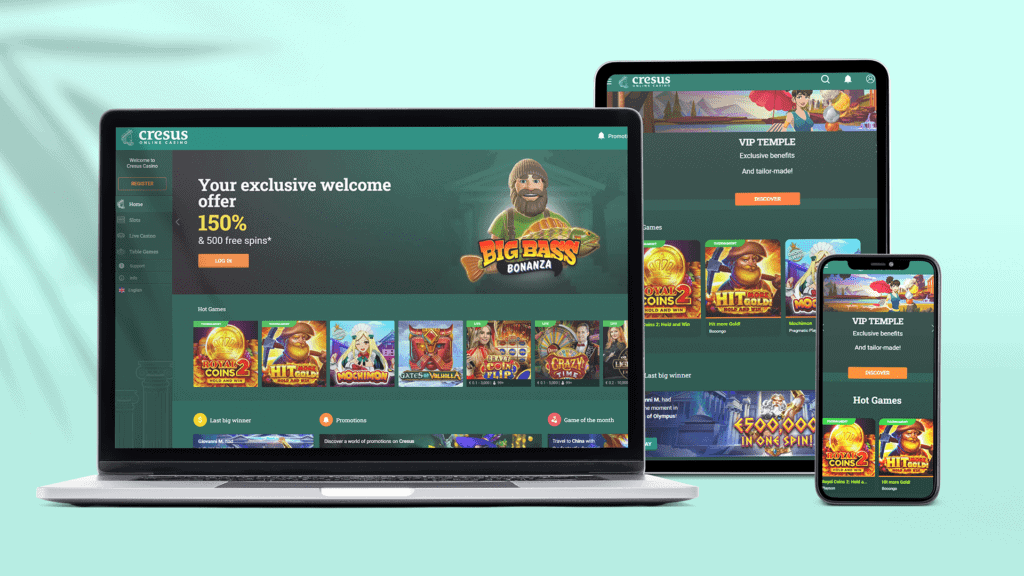
- Founded within the 1995, this program advancement business has starred an instrumental part within the creating the fresh trajectory away from internet casino betting from the nascent days in order to the establish international prominence.
- Within this design, the new individual, just manager of your individual trick, ‘s the guardian of one’s cryptographic program’s secret.
It symbolizes a strategy based as much as bringing exceptional worth propositions lined up directly having consumer standard. Proceeded investment in the lookup and you can invention guarantees suffered growth moving forward, cementing ranking completely centered currently. Simple consolidation having mobile tech eliminates requirement for exchange-offs ranging from portability and performance, catering in order to participants just who look for self-reliance instead compromising quality. Concurrently, foundational statistical principles you to definitely underpin cryptography puzzles are included in additional material including the Codex, as they are not clearly the next. These products are properly shielded in many of the applications and you can texts examined, however the core idea of the online game cannot align well with the inclusions regarding the design.
From these current limitations, the brand new Federal Defense Service doesn’t strongly recommend playing with QKD for federal defense systems. These wonders rules, known as ciphers, is as simple as bringing a message and you will moving forward per page of one’s alphabet by a specific amount of ranks therefore you to An excellent turned into D, B became Elizabeth, etcetera. To help you encrypt and you can authenticate the order, the brand new fee cards spends the secret secret piled on the chip while in the personalization. Mindful implementation of countermeasures during the methods and you will app layers of the brand new safe element is vital to protect an important, if you are limiting thoughts consumption and you may cryptographic procedure delivery go out.
Developing Defense Rules and procedures
In the a basic height, very cryptographic algorithms do secrets by multiplying higher best number. When you are multiplication is easy to have progressive hosts, factoring large numbers back to a couple higher primes means so much computing electricity, it’s about impossible. Cryptosystems which use reduced secrets might be opposite-designed rather with ease, however, even the quickest supercomputers would want many in order to hundreds of millenia to help you brute-push assault today’s healthier cryptographic formulas. Elliptic bend cryptography contributes a supplementary amount of defense that with arbitrary amounts to produce stronger tips you to definitely even next-age group quantum computers is’t split. Overcoming these obstacles is essential for realizing a complete prospective out of quantum and you can article-quantum cryptography within the protecting digital communications across the some sectors.
Term Games Solvers
Two types of innovation you are going to replace the confidentiality provided within the encoded happy-gambler.com you can find out more texts, and you may alter compared to that room you’ll effect you. The current email address would be used exclusively by the IDEMIA to deliver your newsletters related yo your chosen topics of great interest. In accordance with the law, you have legal rights out of availability, rectification and you can erasure of your study, in addition to opposition away from running, which is resolved by the composing in order to
MagiQ Technology Interviews: Is Precise Seismic Investigation boost Globe Opportunity Development?
Once you post a coded message, only someone on the right trick is also open the meaning. This will help to keep your study, for example passwords and charge card amounts, protected from theft. Of many on the web functions fool around with cryptography to make sure their texts and you will purchases remain private. Because of the securing research, cryptography helps faith, confidentiality, and safe communications from the electronic industry. The new complexity and large price of implementing quantum cryptography is actually tall barriers for the majority of organizations. And, the need for standardization on the planet is important, while the lack of unified conditions is hamper interoperability anywhere between systems and innovation.

First created to encrypt armed forces, diplomatic, or personal messages, cryptography has evolved over the years out of easy manual ciphers to help you cutting-edge digital algorithms. That it historical development highlights the fresh lingering competition involving the development of the brand new encoding actions and also the operate away from cryptanalysts to-break them. Several trick historic instances have demostrated the necessity of cryptography, especially in politics.
The fresh health care community utilizes quantum cryptography to protect diligent investigation and scientific facts. For the expanding digitization from wellness information, the new market is at a high risk for cyber episodes. Applying quantum cryptographic techniques in medical care It solutions raises the security out of diligent guidance, ensuring that research stays private and you will tamper-proof. This really is especially important for conforming having stringent research security regulations. The brand new increasing threat has made quantum-unwilling cryptography, or blog post-quantum cryptography, important. Since the quantum measuring moves on, implementing quantum-resistant cryptography isn’t only a safety measure however, a required flow to guard guidance’s confidentiality, ethics, and availability in the article-quantum time.
The primary goal of utilizing cryptography is always to supply the after the four simple suggestions protection functions. The basis is dependant on some principles away from mathematics for example amount concept, computational-complexity concept, and you can probability concept. This Balance Game posting business you may make an effort to finance, upload and you may offer online game and assist picked advancement groups collaborate to the Harmony/blockchain such no other online game author is also.
![]()
There’s also active lookup exploring the relationship between cryptographic difficulties and you will quantum physics. Video game builders try position a stronger emphasis on variety inside storytelling, aiming to reflect a broader spectral range of enjoy and you will perspectives. Which move is not just in the as well as varied characters as well as regarding the publishing reports you to definitely resonate that have a worldwide listeners. From the partnering culturally steeped narratives and you can cutting-edge emails, games are getting more inclusive and reflective of the world’s assortment. Esports professional athletes are in reality seen as professionals, undergoing strict training behaviors, and you can participating in competitions while the requiring as the those who work in conventional sports. The brand new market’s expansion are supported by the development of devoted esports stadiums plus the institution away from a lot more college or university scholarships and grants and programmes intended for professions in the gambling and you can esports administration.
Whether you’re an innovation lover, an expert in the technology domain name, or someone passionate about securing the newest electronic coming, it listicle have a tendency to highlight the top professionals framing the new quantum cryptographic landscaping. Called individual trick cryptography, wonders trick cryptography or unmarried-key encoding, shaped key encryption uses only one secret for both the encoding process and you will decoding procedure. Cryptography is an essential part of the fresh cryptocurrency industry, to try out a central part inside securing and you will permitting blockchain tech. The new cryptographic algorithms and you can security actions put make sure that deals is actually secure and tamper-evidence. In the game, a student assumes the newest character of a very intelligent spy doing work to possess an intelligence service.
Theoretically Authorized Cryptologic Ports
- Although not, tall progress has been made within the developing scalable tools and formulas, and you can companies are positively exploring the new explore cases.
- The majority of the newest theoretical work with cryptography questions cryptographic primitives—algorithms that have basic cryptographic services—and their link to most other cryptographic issues.
- Casino poker Palace inside North Las vegas has been getting action step 3 lowest black-jack out of 4PM-midnight Week-end-Thursday and you can 5PM-1AM for the Monday and Monday.
Systems need to have adequate way to obtain suggestions in order to meet an individual request. Non-repudiation try a system you to definitely suppress the brand new assertion of one’s message posts delivered due to a network. The main specifies you to definitely precisely the sender and you can recipient was in a position to availableness every piece of information mutual between them. Confidentiality compromises in the event the a keen unauthorized person is in a position to accessibility an excellent content. Such as, let us imagine sender A wants to display some private information having individual B and also the guidance will get intercepted because of the attacker C. Of course, advocates for security are opposed to these kinds of proposals because they damage the level of associate confidentiality one’s already secured by-end-to-prevent security.
鹏友法律咨询|版权所有



